1. Login to Oracle Cloud.
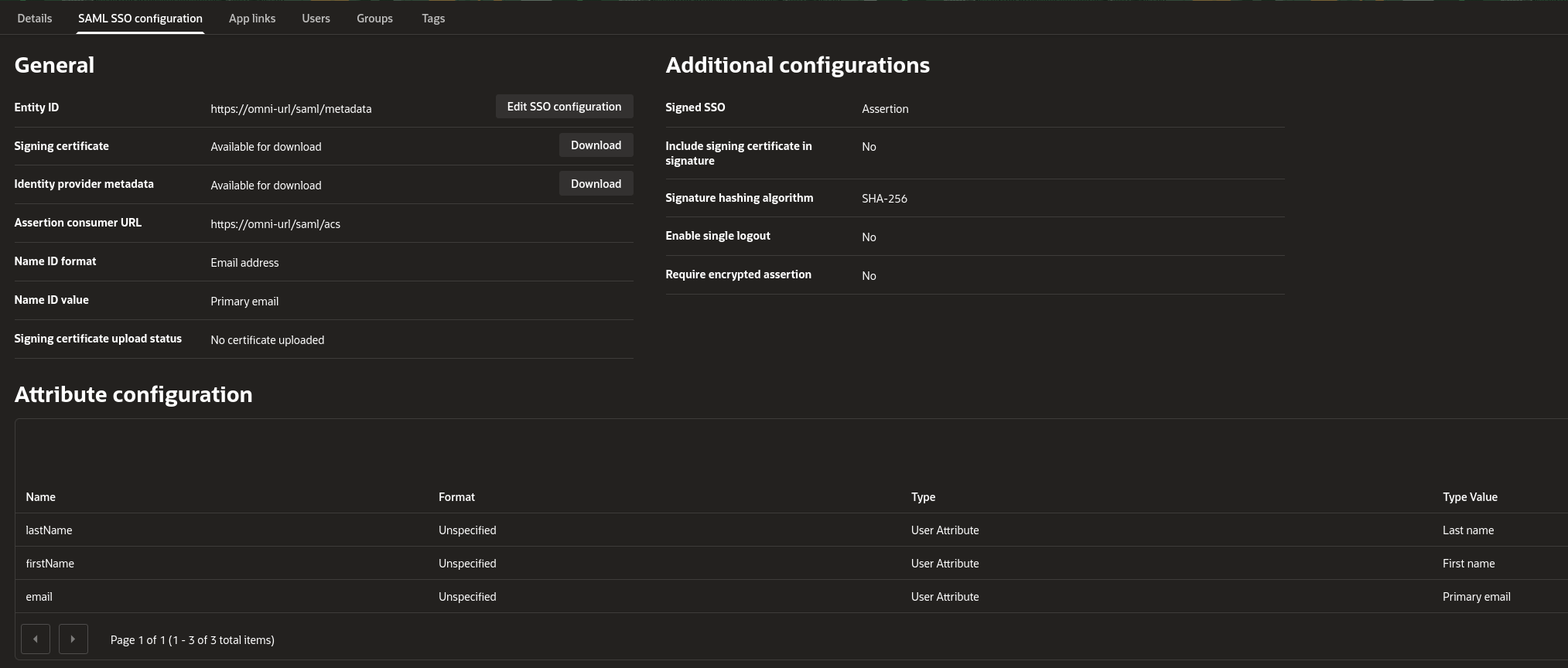
On the left menu, select Identity & Security > Domains. Click your desired domain, then select Integrated Applications. Click Add Application > SAML Application > Launch Workflow. Give the application a name (“Omni” for example) and leave all other fields blank. Select Submit. Select the created application, then click SAML SSO Configuration > Edit SSO Configuration. We can now define our application configuration. Only update the fields mentioned in the table below.| Option | Value | Description |
|---|---|---|
| Entity ID | https://<fqdn for omni>/saml/metadata | The fully-qualified domain name for metadata retrieval |
| Assertion consumer URL | https://<fqdn for omni>/saml/acs | The fully-qualified domain name for acs |
| Name ID Format | Email address | |
| Name ID Value | Primary email | |
| Enable single logout | Disabled |
| Name | Name Format | Value | Description |
|---|---|---|---|
| Unspecified | Primary email | The user’s email address | |
| firstName | Unspecified | First name | The user’s first name |
| lastName | Unspecified | Last name | The user’s last name |
~/oraclemetadata.xml
This completes the configurations required in Oracle Cloud.
2. Configure Omni SAML
To get Omni to use Oracle as a SAML provider, the following flags should be passed to Docker & the Omni container on launch.| Scope | Flag | Description |
|---|---|---|
| Docker | -v $PWD/oraclemetadata.xml:/oraclemetadata.xml | Make available the IDP metadata file in container |
| Omni | --auth-saml-enabled=true | Enable SAML authentication. |
| Omni | --auth-saml-metadata-/oraclemetadata.xml | The path to the IDP metadata file. |
| Omni | --auth-saml-name-id-format=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress | Ensures Omni process the email address correctly. |


 Talos
Talos Omni
Omni Kubernetes Guides
Kubernetes Guides